Protection from spam and malicious messages
With the increasing number and efficacy of malicious e-mail messages, IMS has implemented
several filters to protect you and the institution from spam, viruses, phishing messages,
and other forms of malicious e-mail. This page describes those filters and what you will
experience when a filter is triggered.
NOTE: On July 1, 2015, changes were made to how malicious and
other suspicious messages will be tagged in your inbox. To take up less room on the subject
line and to make the messages more easily readable on mobile devices, most of the tags were
shortened and others made hopefully more insightful. Details of the changes are
described in the topics below.
The HSC employs one of the industry's best spam filters, but it is important to keep in
mind that no spam filter is perfect and some junk messages will get through to your inbox.
Typically, our spam filter detects about 92% of all incoming mail as spam and discards it.
How it works
Our spam filter uses a two-layer approach. First, the source of the incoming connection
is checked against a database of known mail servers around the world. Each server is
scored continuously as to the amount of known-spam, relative volume, and other traits
that would help to identify it as a spam source; this is known as the server’s "reputation
score." We have set thresholds on our servers as to what scores we will block and what
we will accept. If a sending server is somewhere in the "gray area", we will limit it
to 10 messages per hour; this generally allows legitimate messages through but blocks
large bursts of spam from recently-compromised servers. About 90% of all inbound e-mail traffic
is blocked via reputation scoring.
Messages that make it through the reputation filter are then analyzed by anti-spam software.
It looks at the content of the messages for known signatures of spam messages. Like reputation scoring, the anti-spam
software also calculates a score and we have set thresholds for messages that will be
dropped and those that will be accepted. On average, about 20% of the messages that make
it past the reputation filter are subsequently dropped by the spam filter. If a message
falls into the "gray area", we deliver the message to the intended recipient with the
subject line prepended with "[SPAM]". Prior to July 1, 2015, this possible
spam was tagged with "[SUSPECTED SPAM]". On average, about 20% of messages that make it past
the reputation filter are subsequently dropped by the spam filter.
Marketing messages
One problem with spam filtering is discerning between true unsolicited messages (spam) and
messages that are "spam-like" but may be of value to the recipient such as newsletters, purchase
confirmations, listservs, and promotional messages that the recpient has either subscribed to or
is receiving as a result of doing business with a company. These types of bulk messages are not considered
true spam because they are often wanted by the recipient; therefore, we do not universally block
them or flag them as "spam". However, the filter will generally recognize these
and deliver them with the subject line prepended with "[BULK]". Prior to
July 1, 2015, this type of bulk e-mail was tagged as "[SUSPECTECTED MARKETING]". You can use
this subject tag to create a filter or rule in your Inbox to handle these messages as you see fit.
Our central e-mail servers scan the attachments of all incoming messages for known
viruses and other malicious software (malware) using one of the most reputable
anti-malware scanners. If malware is found, the attachment is stripped and replaced
with a text file that contains information about the attachment and virus, generally
either "ATT00001.txt" or "Removed Attachment.txt". In addition, the
subject line of the message is prepended with "[VIRUS REMOVED]". The message is
safe to open, and if you know the sender, you should contact them to alert them that
their computer may be infected.
Unscannable attachments
Sometimes, an attachment may not be able to be scanned due to its size or because it
is password-protected or encrypted. In those cases, we will deliver the e-mail
message and its attachments intact, but we will attach the entire message to a
warning message (“wrapper”) that alerts the recipient that the attachment could
not be scanned and may be malicious. In addition, the subject line will be prepended
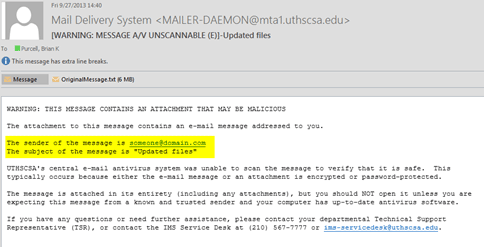
with "[WARNING: MESSAGE A/V UNSCANNABLE]". If you receive one of these messages,
you should carefully evaluate the sender of the message and the subject-- which are
listed in the “wrapper” as shown below-- to determine if the message is safe to open:
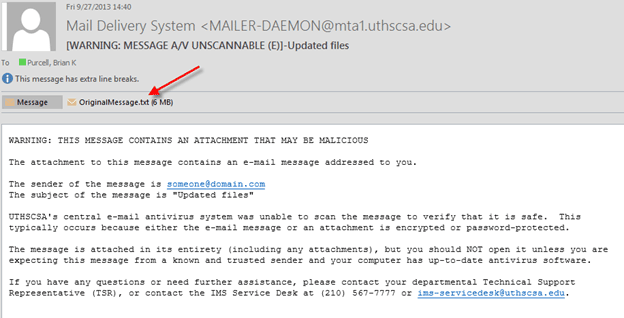
If you recognize the sender and were expecting the attachment, double-click the
attachment entitled "OrignialMessage.txt"; this will contain the original message
in its entirety, including the attachments:
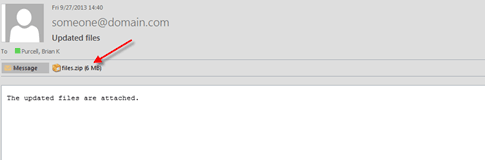
You should then evaluate the message and attachment again to ensure they look
legitimate; if in doubt, delete the message or forward the message to the IMS Service
Desk for further evaluation at spam@uthscsa.edu.
Otherwise, you can open the attachment as you normally would, although we recommend
saving it to your computer or a file server first so that it will be scanned again
by your computer’s antivirus software as an extra layer of protection.
MALICIOUS MESSAGES (Phishing, scams, etc.)
Messages that pass the spam and virus scanning are further scanned for suspicious content
that does not yet have a known virus or spam signature. These messages can include
phishing messages and scams, new viruses, or links to websites with malicious content
(malware). This feature provides enhanced protection against new and evolving e-mail
threats above and beyond our existing spam and virus scanning.
How it works
This feature uses heuristics or artifical intelligence to look for suspicious traits within messages.
When a suspicious message is detected, it is quarantined for a brief period of time
(less than four hours typically) to allow for the message to be rescanned periodically
using updated spam and virus signatures. After the quarantine period expires, the
message is released to the recipient but the subject is prepended with “[SUSPICIOUS]” and
any URLs (links) in the message are modified to redirect through a web-based
scanning service where the contents of the suspect web page are analyzed. Prior to
July 1, 2015, this questionable message was tagged with "[SUSPICIOUS MESSAGE]".
While the page is being scanned, you will see this message:
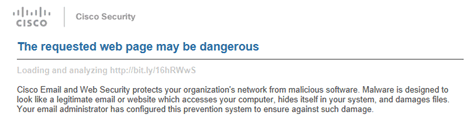
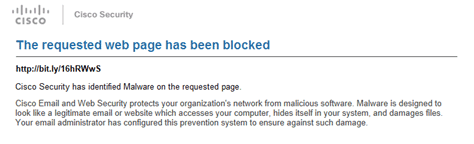
This scan typically only takes a few seconds. If the web page is malicious, it will
be blocked and you will receive this message:
If the page is determined to likely not be malicious, you will be shown a copy of the
page with an option overlaid to either continue to the site or to not:
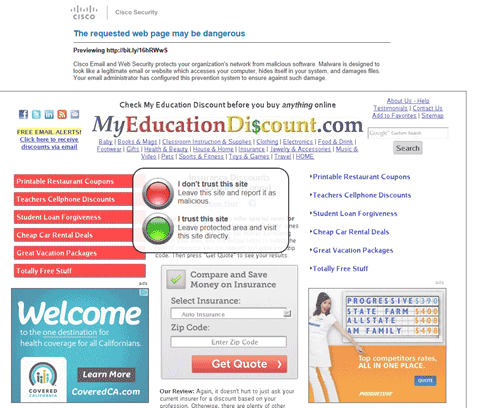
Because the analysis and initial presentation of the page is done on a protected server
and not done on your computer or device, it protects you from any potential malicious
activity while you determine the legitimacy of the site. If you’re unsure as to the
safety of the site, you should err on the side of caution and opt not to trust it.
Note: The web address of the protected server begins with
https://secure-web.cisco.com;
this is the address you will see in your browser’s address bar while the site is analyzed.
This is a web-based product and should work on all types of computers and devices.
The filtering described above takes place on UTHSCSA's central e-mail gateways.
If you’re using Outlook, it has its own built-in junk mail filter and once messages reach your mailbox,
Outlook performs its own spam filtering based on filters from Microsoft as well as any mailbox rules you've
configured. Messages that are identified as spam via this filtering are typically put into the "Junk E-mail"
folder. You should check this folder periodically for any legitimate messages that may have been misdiagnosed.
With a couple of exceptions, this filtering
is not centrally-managed; more information on using this filter is available on
Microsoft’s website at
http://office.microsoft.com/en-us/outlook-help/overview-of-the-junk-email-filter-HP010355048.aspx.
If you have any questions or need further assistance, please contact the IMS Service
Desk at (210) 567-7777 or ims-servicedesk@uthscsa.edu.